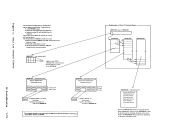
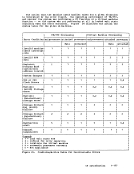
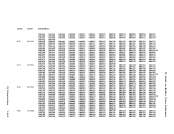
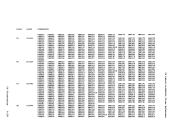
If the operation active on the virtual device is
in the realequipment, the simulation of a HIO or
involved, since itrequires the actual execution of
this case, the active operation is halted and the
code/status is returned to the user.
actually in progressHDV is somewhat more
the instruction. In
resultant condition
The virtual channe1-to-channe1 adapter (CTCA) simulates data transfer
and control communication betweentwo selector channels, either on two distinct processors or two channels on a single processor. Data
transfer is accomplished via synchronized complementaryI/O commands
(forexample, read/write, write/read) issued to both parts of the CTCA.
Each part of the CTCA is identical and the operation of the unit is
completely sy•• etrica1. The CTCA occupies an entire control unit slot
on each of the two channels attached. Therightmost four bits of the
unit address (device address) are ignored completely and are notavai~able for use.
TheV8/310 control program support for virtual CTCA includes all
status, sense data, and interruption logic necessary to simulate the
operation of the real CTCA. Data transfer,command byte exchange, sense
data, and status data presentation for the virtual CTCA is accomplished
via storage-to-storage operations(8VCL,etc.). No real I/O operations
(excluding pagingI/O) nor I/O interruptions are involved. Unit errors
or control errors cannot occur.
TheCCW translator, D8KCCWTR, is called by the virtual machine I/O executive program (D8KYSIEX) when an I/O task block has been created and
a list of virtualCCls associated with a user's 510 request .ust be
translated into realCCls. When the I/O operation from a self-modifying channel program is
completed,D8KUNTIS is called by DKKIOS. When retrans1ation of OS ISA8 CCWs is required, the self-modifying channel program checking portion of D8KCCWTR calls D8KIS8TR. D8KCCWTR operates in two phases: • A scan and a trans1a te phase. • A TIC-scan phase. 1 self-modifying channel program checking function is also included.
The scan and translate phase analyzes the virtua1CCW list. So.e channel co •• ands require additional doub1ewords fo.r control information
(forexample, seek addresses). Additional ·contro1 words are also
allocated (in pairs) if the data area specified by a virtualCCW crosses 4096-byte page boundaries, or if the virtual CCW includes an IDA
(indirect data address) flag.Space is obtained from D8KFREE for the real CCI list, and the
translation phase then translates the virtualCCW list into a real CCW list. TIC commands that cannot be i.mediate1y translated are flagged for
later processing by the TIC-scan phase.A READ or WRITE com.and that
1-86IBK VK/310 System Logic and Problem Determination--Vo1u.e 1
in the real
involved, since it
this case, the active operation is halted and the
code/status is returned to the user.
actually in progress
the instruction. In
resultant condition
The virtual channe1-to-channe1 adapter (CTCA) simulates data transfer
and control communication between
transfer is accomplished via synchronized complementary
(for
Each part of the CTCA is identical and the operation of the unit is
completely sy
on each of the two channels attached. The
unit address (device address) are ignored completely and are not
The
status, sense data, and interruption logic necessary to simulate the
operation of the real CTCA. Data transfer,
data, and status data presentation for the virtual CTCA is accomplished
via storage-to-storage operations
(excluding paging
or control errors cannot occur.
The
a list of virtual
translated into real
completed,
The scan and translate phase analyzes the virtua1
(for
allocated (in pairs) if the data area specified by a virtual
(indirect data address) flag.
translation phase then translates the virtual
later processing by the TIC-scan phase.
1-86