A CP routine must lock another virtual machine for any of the
following reasons:
1. The routine, or a routine it calls, accesses any unshared page of
the virtual machine.
2. The routine, or a routine it calls, alters any field of theVMBLOK that is serialized only by the VMBLOK lock.
3. The routine, or a routine it calls, could be interrupted and an
exit taken to the dispatcher.
The originalYMBLOK lock must be released before gaining the new
lock.
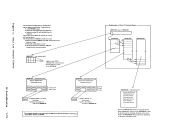
Figure 23 shows the modules that obtain theVMBLOK lock for a virtual
machine other than the one requesting the service.
There are situations when aCP routine may access a virtual machine without locking it. If the CP routine, or any routine it calls, is only
alteringVMBLOK fields that are serialized by the system lock, locking
the virtual machine is not necessary. For example, to process theSET PRIORITY command for a virtual machine, locking the virtual machine is
not necessary since the alteredVMBLOK field, VMUPRIOR, is serialized by
the system lock. But to process theSET FAVORED com.and, locking the
virtual machine is necessary since some of theV!BLOK fields altered,
such asVMRSTAT, are only serialized by the VMBLOK lock. DMKLOKFR DMKLOKRL DMKLOKTR DMKLOKDS Free Storage Lock
Run List Lock
Timer Request Queue Lock
Dispatcher Queues LockCPEXBLOK Queue Lock
deferred execution blocks
processor related blocks
IOBLOK/TRQBLOK Queue Lock
These are system spin locks that are held for very short periods oftime. The control program code that runs without the global system lock must manipulate these queues and these locks insure system integrity
along the unlocked paths.
Ifyou have user-defined areas that are used by more than one virtual
machine andyou need to serialize their use, you will need to define
your own locking conventions.You can use the LOCK macro to obtain and
release aPRIVATE lock. VML370 ~I§!~A f£ogr~!!~~~~ 2uig~ has details on
how to code the LOCK macro.
MACHINE CHECK HANDLER IN ATTACHEDPROCESSOR A machine check interrupt is initially handled without the global system lock. DMKMCH determines if the error requires system termination,
virtual machine termination, orsimply recording and continuation. If
thesystem was in a wait state or a virtual machine was in control and
the system is not to be terminated, the machine check handler requests
the global system lock with the defer option. If the lock can be
1-114IBM YM/370 System Logic and Problem Determination--Voluae 1
following reasons:
1. The routine, or a routine it calls, accesses any unshared page of
the virtual machine.
2. The routine, or a routine it calls, alters any field of the
3. The routine, or a routine it calls, could be interrupted and an
exit taken to the dispatcher.
The original
lock.
Figure 23 shows the modules that obtain the
machine other than the one requesting the service.
There are situations when a
altering
the virtual machine is not necessary. For example, to process the
not necessary since the altered
the system lock. But to process the
virtual machine is necessary since some of the
such as
Run List Lock
Timer Request Queue Lock
Dispatcher Queues Lock
deferred execution blocks
processor related blocks
IOBLOK/TRQBLOK Queue Lock
These are system spin locks that are held for very short periods of
along the unlocked paths.
If
machine and
your own locking conventions.
release a
how to code the LOCK macro.
MACHINE CHECK HANDLER IN ATTACHED
virtual machine termination, or
the
the system is not to be terminated, the machine check handler requests
the global system lock with the defer option. If the lock can be
1-114