specifies that data cross 4096-byte boundaries is revised to include an
IDA flag that points to an indirect data address list (IDAL) and a pair
of words for each 4096-byte page, in which each word handles a data
transfer of2048 bytes (or less). The real CCI is flagged as having a
CP-generated IDA.DMKPTRAN is called (via the TRANS macro) to lock each 4096-byte page.
If the realCCI string does not fit in the allocated free storage
block, a new block is obtained. The old block is transferred and
adjusted before being released._ The translation continues with the new
block. The process is repeated, as needed, to contain the realCCW string. Virtual CCWs having an IDA flag set are converted to user translated
addresses for each IDAi (indirect data address word) in the virtual
IDAL.DMKPTRAN is called for each IDAW is. The CCW is flagged as having a user (but not CP) generated IDA. The TIC-scan phase scans the real CCW list for flagged (untranslated)
TIC commands and creates a new virtualCCi list for the untranslated
coamands._ Scan-translate phase processing is then repeated. When all
virtualCCWs are translated, the virtual CAW in the IOBLOK task block is
replacedby the real CAW (that is, a pointer to the real CCW list
created byDMKCCWTR), and DMKCCWTR returns control to DMKVIOEX. The
user protectionkey is saved.
Because many of theOS PCP, MFT, and MVT ISAM channel prograas are
self-aodifying, special handling is requiredby the VM/370 control
program to allow virtual machines to use this access method. The
particularCCWs that require special handling have the following general
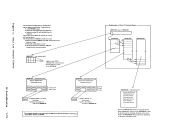
foraat:0 2 4 6 8
11
RE1DD1TlCf-7 10 hv+oC! A "'.1. --...,. I B TIC to E I C I I D I I E SEEK: SEEK head on D I I F SEARCB on Dt-2 The cei at ! reads 10 bytes of data. The tenth byte foras the coamand code of the CCi at E. In addition, the data read in aakes up
the seek and search arguaents for theCCWs at E and F. After the CCW string is translated by the VM/370 control prograa, it usually is in the
following foraat:
CP Introduction 1-87
IDA flag that points to an indirect data address list (IDAL) and a pair
of words for each 4096-byte page, in which each word handles a data
transfer of
CP-generated IDA.
If the real
block, a new block is obtained. The old block is transferred and
adjusted before being released.
block. The process is repeated, as needed, to contain the real
addresses for each IDAi (indirect data address word) in the virtual
IDAL.
TIC commands and creates a new virtual
coamands.
virtual
replaced
created by
user protection
Because many of the
self-aodifying, special handling is required
program to allow virtual machines to use this access method. The
particular
foraat:
11
RE1DD1Tl
the seek and search arguaents for the
following foraat:
CP Introduction 1-87