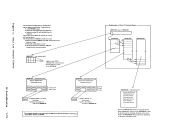
EBCDIC.
user address obtained from the address portion of the virtual
the next
constructed in the
the
the output
located
the data buffer. The
the buffer and provide the necessary length, translation, and foraat
functions. Control is
the writing. At this point, the virtual
chaining is specified, processing continues to fetch and analyze the
next
constructed in the
the
An
equipment; thus, a aessage indicating the
constructed.
the command is chained, processing continues (for
the next
this is not the first
first (and only)
channel end and device end in the virtual
The sense data fro. the
location specified in the virtual
chained, processing continues to fetch the next
If the fetched
channel
as an interruption or as a
address and analyzes the fetched
is reflected to the virtual machine
Invalid
terminated with unit check status presented in the virtual
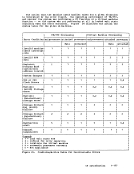
contained in
and General
CP Introduction 1-97