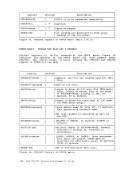
THE SENDI PROTOCOL The SENDI protocol defines a transaction calling for an expedited
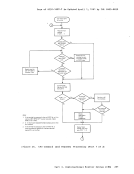
one-way transfer of data. Figure 17shows the SENDX protocol
graphically.SENDI differs from the SEND protocol in that the sink
virtual machine need not issue theRECEIVE subfunction; data is
transferred from source virtualmachine storage to sink virtual machine
storage at the same time the external interrupt from CP notifies the
sink virtual machine of the transaction. Data sent by the source
virtual machine is placed in the external interrupt buffer of the sink
virtual machine.Virtual machines using the SENDX protocol are responsible for
specifying the userid for the sink virtual machine, a message ID, the
address and length of the data being sent, and the external interrupt
buffer address and data length for the sink virtual machine.A virtual machine to be used as a sink virtual machine with the SENDX protoccl
aust specify this informationVMCPARM when that virtual machine
issues theAUTHORIZE subfunction. The data length specified must be at
least as long as the maximum amount of data to be transferred during a
transaction; it need not belimited to the usual 40-byte external
interrupt buffer. Effective use of theSENDI protocol requires that VMCF users agree on a maximum size for SEND X data and then issue the AUTHORIZE subfunction with the appropriate external interrupt buffer
size.
If the sink virtualmachine has not provided enough SENDX buffer area
in the external interrupt buffer, CP notifies the source virtualmachine that the transaction was not completed. When a SENDI data transfer is complete, CP directs a response
external interrupt to the source virtual machine, notifying it that the
transaction is complete.
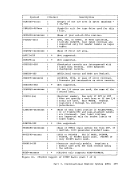
rI DMKVMC I I VMCF I Interface I Module Source Virtual Machine , I I I I I I I SENDX------)----------)I I -----------------)Data I I I I <--External Interrupt--I (Final Response) t I I Figure 17. The SENDX Protocol I I I I I I I I Sink Virtual Machine I Transfer-------------------) I I --External Interrupt-----) I (Buffer Contains Data)
Part 2. ControlProgram (CP) 151
one-way transfer of data. Figure 17
graphically.
virtual machine need not issue the
transferred from source virtual
storage at the same time the external interrupt from CP notifies the
sink virtual machine of the transaction. Data sent by the source
virtual machine is placed in the external interrupt buffer of the sink
virtual machine.
specifying the userid for the sink virtual machine, a message ID, the
address and length of the data being sent, and the external interrupt
buffer address and data length for the sink virtual machine.
aust specify this information
issues the
least as long as the maximum amount of data to be transferred during a
transaction; it need not be
interrupt buffer. Effective use of the
size.
If the sink virtual
in the external interrupt buffer, CP notifies the source virtual
external interrupt to the source virtual machine, notifying it that the
transaction is complete.
r
Part 2. Control