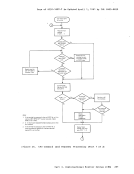
to the real processor more frequently than those that are not; these
conversational machines are assigned the smaller of two possible time
slices. CP determines execution characteristics of a virtual machine at
the end of each time slice on the basis of the recent frequency of its
console requests or terminal interrupts. The virtual machine is queued
for subsequent processor utilization according to whether it is a
conversational or nonconversational user of system resources.
A virtual machine can gain control of the processor only if it is not
waiting for some activity or resource. The virtual machine itself may
enter a virtual wait state after an input/output operation has begun.
The virtual machine cannot gain control of the real processor if it is
waiting for a page of storage, if it is waiting for an input/output
operation to be translated and started, or if it is waiting for a CP
command to finish execution.
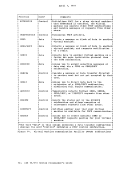
A virtual machine can be assigned a priority of execution. Priority
is a parameter affecting the execution of a particular virtual machine
as compared with other virtual machines that have the same general
execution characteristics. Priority is a parameter in the virtual
machine's
value with the privilege class A
part of the virtual machine configuration in the
and not greater than the maximum defined value.
storage as virtual storage. The storage may appear as paged or unpaged
to the virtual machine, depending upon whether or not the extended
control mode option was specified for that virtual machine. This option
is required if operating systems that control virtual storage, such as
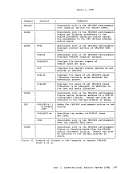
Storage in the virtual machine is logically divided into 4096-byte
areas called pages. A complete set of segment and page tables is used
to describe the storage of each virtual machine. These tables are
updated by CP and reflect the allocation of virtual storage pages to
blocks of real storage. These page and segment tables allow virtual
storage addressing in a
is logically and physically divided into 4096-byte areas called page
frames.
Only referenced virtual storage pages are
optimizing real storage utilization. Further, a page can be brought into
any available page frame; the necessary relccation is done during
program execution by a combination of
translation on the System/370. The active pages from all logged on
virtual machines and from the pageable routines of CP compete for
available page frames.
allocation falls below a threshold value, CP determines which virtual
storage pages currently allocated to real storage are relatively
inactive and initiates suitable page-out operations for them.
76