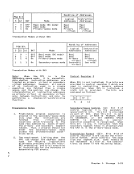
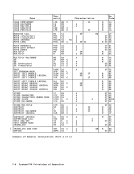
R t 1////////1 First-Operand Address 0 8 31
R t + 11////////1 First-Operand Length 0 8 31 R2 1////////1 Second-Operand Addressl 0 8 31 R2 + 1
Pad Second-Operand Length0 8 31
The movement starts atthe left end of
both fields and proceeds to the right.
The operation is ended when the number
of bytes specified by bit positions 8-31
of general register Rt + 1 have been
moved into the first-operand location.
If the second operand is shorter than
the first operand, the remaining right
most bytes of the first-operand location
are filled with the padding byte.
As part of the execution of the instruction, the values of the two length
fields are compared for the setting of
the conditioncode, and a check is made
for destructive overlap of the operands.
Operands are said to overlap destruc
tively whenthe first-operand location
is used as a source after data hasbeen moved into it, assuming the inspection
for overlap is performed by the use of
logical operand addresses. When the
operands overlap destructively, no move
ment takesplace, and condition code 3
is set.Operands do not overlap destructively,
and movement isperformed, if the left
most byte of the first operand does not
coincide with any of the second-operand
bytes participating in the operation
other than the leftmost byte of the
second operand. When an operand wraps
around from location 16,777,215 to
location0, operand bytes in locations
up to and including 16,777,215 are
considered tobe to the left of bytes in
locations from0 up.
When the length specified by bit posi
tions 8-31 of general registerRI + 1 is zero, no movement takes place, and
condition code0 or 1 is set to indicate
the relative values of the lengths.
instruction is The execution of the
interruptible.When occurs other than one
nation, the contents
ters Rt + 1 andR2 +
an interruption
that causes termi
of general regis-
1 are decremented
by the number of bytes moved, and the
contents of general registers Rt andR2 are incremented by the same number, so
that the instruction, whenreexecuted, resumes at the point of interruption. The leftmost bits which are not part of
the address in general registersR, and
R2 are set to zeros; the contents of bit
positions0-7 of general registers R, + 1 and R2 + 1 remain unchanged; and
the condition code is unpredictable. If
the operation is interrupted during
padding, the length field in general
register R2 + 1 is0, the address in
general register R2 is incremented by
the original contents of general regis
ter R2 +1, and general registers Rt and R, + 1 reflect the extent of the padding
operation.
When the first-operand location includes
the location of the instruction or of
EXECUTE, the instruction may be
refetched from storage and reinterpretedeven in the absence of an interruption
during execution. The exact point in
the execution at which such a refetch
occurs is unpredictable.
As observed by otherCPUs and by chan
nels, that portion of the first operand
which is filled with the padding byteis not necessarily stored into in a left
to-right direction and may appear to be
storedinto more than once.
At the completion of the operation, the
length in general registerR, + 1 is
decremented by the number of bytes
stored at the first-operand location,
and the address in general register Rt
is incremented by the same amount. The
length in general register R2 + 1 is
decremented by the number of bytes moved
out of the second-operand location, and
the address in general registerR2 is
incremented by the same amount. The
leftmost bits which are not part of the
address in general registersR, and R2 are set to zeros, including the case
when one or both of the original length
values are zeros or when condition code
3 is set. The contents of bit positions0-7 of general registers Rt + 1 and
R2 + 1 remain unchanged.
When condition code 3 isset, no
exceptions associated with operand
access are recognized. When the length
of an operand is zero, no access
exceptions for that operand are recog-
nized. Similarly, when the second
operand is longer than the first
operand, access exceptions are not
recognized for the part of the second
operand field that is in excess of the
first-operand field. For operands long
er than 2K bytes, access exceptions are
not recognized for locations more than
2K bytes beyond the current location
being processed. Access exceptions are
not recognized for an operand if the R
field associated with that operand is
odd.Also, when the R, field is odd, Chapter 7. General Instructions 7-25
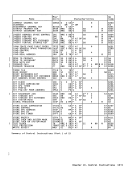
R t + 1
Pad Second-Operand Length
The movement starts at
both fields and proceeds to the right.
The operation is ended when the number
of bytes specified by bit positions 8-31
of general register Rt + 1 have been
moved into the first-operand location.
If the second operand is shorter than
the first operand, the remaining right
most bytes of the first-operand location
are filled with the padding byte.
As part of the execution of the instruc
fields are compared for the setting of
the condition
for destructive overlap of the operands.
Operands are said to overlap destruc
tively when
is used as a source after data has
for overlap is performed by the use of
logical operand addresses. When the
operands overlap destructively, no move
ment takes
is set.
and movement is
most byte of the first operand does not
coincide with any of the second-operand
bytes participating in the operation
other than the leftmost byte of the
second operand. When an operand wraps
around from location 16,777,215 to
location
up to and including 16,777,215 are
considered to
locations from
When the length specified by bit posi
tions 8-31 of general register
condition code
the relative values of the lengths.
instruction is The execution of the
interruptible.
nation, the contents
ters Rt + 1 and
an interruption
that causes termi
of general regis-
1 are decremented
by the number of bytes moved, and the
contents of general registers Rt and
that the instruction, when
the address in general registers
R2 are set to zeros; the contents of bit
positions
the condition code is unpredictable. If
the operation is interrupted during
padding, the length field in general
register R2 + 1 is
general register R2 is incremented by
the original contents of general regis
ter R2 +
operation.
When the first-operand location includes
the location of the instruction or of
EXECUTE, the instruction may be
refetched from storage and reinterpreted
during execution. The exact point in
the execution at which such a refetch
occurs is unpredictable.
As observed by other
nels, that portion of the first operand
which is filled with the padding byte
to-right direction and may appear to be
stored
At the completion of the operation, the
length in general register
decremented by the number of bytes
stored at the first-operand location,
and the address in general register Rt
is incremented by the same amount. The
length in general register R2 + 1 is
decremented by the number of bytes moved
out of the second-operand location, and
the address in general register
incremented by the same amount. The
leftmost bits which are not part of the
address in general registers
when one or both of the original length
values are zeros or when condition code
3 is set. The contents of bit positions
R2 + 1 remain unchanged.
When condition code 3 is
exceptions associated with operand
access are recognized. When the length
of an operand is zero, no access
exceptions for that operand are recog-
nized. Similarly, when the second
operand is longer than the first
operand, access exceptions are not
recognized for the part of the second
operand field that is in excess of the
first-operand field. For operands long
er than 2K bytes, access exceptions are
not recognized for locations more than
2K bytes beyond the current location
being processed. Access exceptions are
not recognized for an operand if the R
field associated with that operand is
odd.