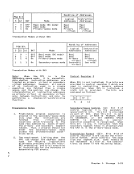
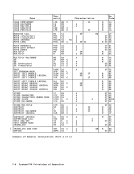
a location in the corresponding storage
block is referred to either for storing
or for fetching of information.Change Bit (~): The change bit, bit 6, is set to one each time information is
stored at alocation in the correspond
ing storage block.
Storage keys are not part of addressable
storage. Provided that the storage-key
4K-byte-blockfacility is not installed,
a storage keyis associated with each
2K-byte block of storage. The entire
storage key is set by SETSTORAGE KEY and inspected by INSERT STORAGE KEY. Additionally, the instruction RESET
REFERENCE BIT providesa means of
inspecting the reference and change bits
and of setting the reference bit to
zero. Bits0-4 of the storage key are
inspected by the INSERT VIRTUALSTORAGE KEY instruction. The contents of the
storage key are unpredictable during and
after the execution ofthe usability
test of the TESTBLOCK instruction. STORAGE-KEY 4K-BYTE-BLOCK FACILITY
Depending on whether the storage-key
4K-byte-block facilityis installed, one
or two storage keys are associatedwith each 4K-byte block of storage that is in
the configuration. The storage-key
exception controlis also provided as
part ofthis facility.
storage Keys with Storage-Key
4K-Byte-Block Facility Not Installed
When the storage-key 4K-byte-block
facility is not installed, two keys are
associated with the block,and the block is called a double-key 4K-byte block.
Ina double-key 4K-byte block, one key is associated with the first 2K-byte
block and one with the second 2K-byte
block. The keysare referred to as the
low-order and high-order keys, just as
the two 2K-byte blocksare referred to
as the low-orderand high-order 2K-byte
blocks. The instructions INSERTSTORAGE KEY, RESET REFERENCE BIT, and SET STOR AGE KEY designate a 2K-byte block and
operate on the high-order or low-order
key, whichever is addressed. The
instructions INSERTSTORAGE KEY EXTENDED, RESET REFERENCE BIT EXTENDED,
and SETSTORAGE KEY EXTENDED designate a 4K-byte block and operate on both the
high-order and low-order keys.
Storage Keys with Storage-Key
4K-Byte-Block Facility Installed
When the storage-key 4K-byte-block
facility is installed, only one key isassociated with a 4K-byte block, and it
is calleda single-key 4K-byte block.
In a single-key 4K-byte block, the
single keyis associated with both
2K-byte blocks. The instructions INSERTSTORAGE KEY EXTENDED. RESET REFERENCE
BIT EXTENDED, and SETSTORAGE KEY EXTENDED operate on the single key of the block. The action taken when the
instructions INSERTSTORAGE KEY, RESET
REFERENCE BIT, and SETSTORAGE KEY are executed depends upon the setting of the
storage-key-exception control, bit 7 of
control registerO. Storage-Key-Exception Control
When the storage-key 4K-byte-block
facility is installed, bit 7 of control
register0, the storage-key-exception
control bit, controls the execution of
the instructions INSERTSTORAGE KEY, RESET REFERENCE BIT, and SET STORAGE KEY. If the bit is zero, a special
operation exceptionis recognized. If
the bitis one, the operation is
performed on the single keyassociated with the 4K-byte block.
When the storage-key 4K-byte-block
facility is not installed, astorage key
isassociated with each 2K-byte block,
and bit 7 of control register0 is
ignored.STORAGE-KEY-INSTRUCTION EXTENSIONS The storage-key-instruction-extension
facility includes the three instructions
INSERTSTORAGE KEY EXTENDED, RESET
REFERENCE BIT EXTENDED, and SETSTORAGE KEY EXTENDED. These instructions
provide operations similar to those of
INSERTSTORAGE KEY, RESET REFERENCE BIT,
and SETSTORAGE KEY, except that they
operate on both single-keyand double
key 4K-byte blocks without reference tothe state of the storage-key-exception
control bit and providea 31-bit real
address.PROTECTION Three protection facilities are provided
to protect the contents of main storage
from destruction or misuse by programs
that contain errors or are unauthorized:
key-controlled protection, segment
protection, and low-address protection.
Chapter 3. Storage 3-7
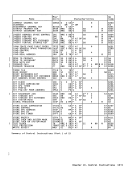
block is referred to either for storing
or for fetching of information.
stored at a
ing storage block.
Storage keys are not part of addressable
storage. Provided that the storage-key
4K-byte-block
a storage key
2K-byte block of storage. The entire
storage key is set by SET
REFERENCE BIT provides
inspecting the reference and change bits
and of setting the reference bit to
zero. Bits
inspected by the INSERT VIRTUAL
storage key are unpredictable during and
after the execution of
test of the TEST
Depending on whether the storage-key
4K-byte-block facility
or two storage keys are associated
the configuration. The storage-key
exception control
part of
storage Keys with Storage-Key
4K-Byte-Block Facility Not Installed
When the storage-key 4K-byte-block
facility is not installed, two keys are
associated with the block,
In
block and one with the second 2K-byte
block. The keys
low-order and high-order keys, just as
the two 2K-byte blocks
as the low-order
blocks. The instructions INSERT
operate on the high-order or low-order
key, whichever is addressed. The
instructions INSERT
and SET
high-order and low-order keys.
Storage Keys with Storage-Key
4K-Byte-Block Facility Installed
When the storage-key 4K-byte-block
facility is installed, only one key is
is called
In a single-key 4K-byte block, the
single key
2K-byte blocks. The instructions INSERT
BIT EXTENDED, and SET
instructions INSERT
REFERENCE BIT, and SET
storage-key-exception control, bit 7 of
control register
When the storage-key 4K-byte-block
facility is installed, bit 7 of control
register
control bit, controls the execution of
the instructions INSERT
operation exception
the bit
performed on the single key
When the storage-key 4K-byte-block
facility is not installed, a
is
and bit 7 of control register
ignored.
facility includes the three instructions
INSERT
REFERENCE BIT EXTENDED, and SET
provide operations similar to those of
INSERT
and SET
operate on both single-key
key 4K-byte blocks without reference to
control bit and provide
address.
to protect the contents of main storage
from destruction or misuse by programs
that contain errors or are unauthorized:
key-controlled protection, segment
protection, and low-address protection.
Chapter 3. Storage 3-7