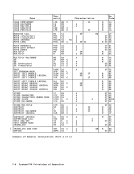
bits 8-27 of the ASN-first-table entry
and adding theASX portion with four
rightmost and 14 leftmost zeros
appended. A carry, if any, into bit
position 7is ignored. With extended
real addressing, this 24-bit real
address is extended on the left with
zeros; thus, the ASN-second table can
wrap from 224 -1 to zero.
The 16 bytes of the ASN-second-table
entry appear to be fetched word
concurrentas observed by other CPUs, with the leftmost word fetched first.
The order in which the remaining three
words are fetched is unpredictable. The
fetch accessis not subject to
protection. When the storage address
which is generated for fetching the
ASN-second-table entry designates a
location which is not available in the
configuration, an addressing exception
is recognized, and the operationis suppressed.
Bit0 of the 16-byte ASN-second-table
entry specifies whether the address
space is accessible. If this bitis one, an ASX-translation exception is
recognized. If bit positions 1-7,30, 31, 60-63, and 97-103 of the ASN
second-table entry do not contain zeros,
an ASN-translation-specification excep
tionis recognized.
Recognition of Exceptions during ASN
Translation
The exceptions which can be encountered
during the ASH-translation process are
collectively referred to asASH translation exceptions. A list of these
exceptions and their priorities is givenin Chapter 6, "Interruptions." ASH AUTHORIZATION ASH authorization is the process of
testing whether the program associated
with the current authorization indexis permitted to establish a particular
address space. TheASH authorization is performed as part of PROGRAM TRANSFER
with space switching (PT-ss) and SETSECONDARY ASH with space switching
(SSAR-ss) and may be performed as part
ofLOAD ADDRESS SPACE PARAMETERS. ASN
authorizationis performed after the ASH-translation process for these
instructions.
When performed as part of PT-ss, theASH authorization tests whether the ASH can
be established as the primaryASH and is called primary-ASH authorization. When
performed as part ofLOAD ADDRESS SPACE PARAMETERS or SSAR-ss, the ASH authori zation tests whether the ASH can be
established as the secondaryASN and is
called secondary-ASN authorization.
TheASN authorization is performed by
means of an authority table in real
storage which is designated by the
authority-table-origin and authority
table-length fieldsin the ASN-second
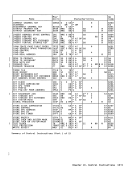
table entry.ASH-AUTHORIZATION COHTROLS ASN authorization uses the authority
table origin and the authority-table
length from the ASH-second-table entry,
together with an authorization index.Control Register ~ For PT-ss and SSAR-ss, the current
contents of control register 4 include
the authorization index. ForLOAD ADDRESS SPACE PARAMETERS, the value
which will become the new contents of
control register 4;s used. The regis
ter has the following format:
AXa 15
Authorization Index (AX): Bits0-15 of
control register 4 are used as an index
to locate the authority bits in the
authority table.
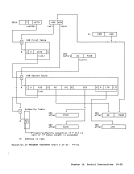
ASN-Second-Table Entry
The ASN-second-table entry which is
fetched as part of theASH translation
process contains information which is
used to designate the authority table.
An entryin the ASN second table has the
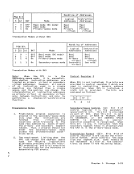
following format:100000001 ATO 1
00 I o 1 8 31
ATl1
0000 I 32 48 60 64
Authority-TableOrigin (ATO): Bits
8-29, with two zeros appended on the
right, are used to forma 24-bit real
address that designates the beginning of
the authority table.With extended real
addressing, the authority-table originChapter 3. Storage 3-17
and adding the
rightmost and 14 leftmost zeros
appended. A carry, if any, into bit
position 7
real addressing, this 24-bit real
address is extended on the left with
zeros; thus, the ASN-second table can
wrap from 224 -1 to zero.
The 16 bytes of the ASN-second-table
entry appear to be fetched word
concurrent
The order in which the remaining three
words are fetched is unpredictable. The
fetch access
protection. When the storage address
which is generated for fetching the
ASN-second-table entry designates a
location which is not available in the
configuration, an addressing exception
is recognized, and the operation
Bit
entry specifies whether the address
space is accessible. If this bit
recognized. If bit positions 1-7,
second-table entry do not contain zeros,
an ASN-translation-specification excep
tion
Recognition of Exceptions during ASN
Translation
The exceptions which can be encountered
during the ASH-translation process are
collectively referred to as
exceptions and their priorities is given
testing whether the program associated
with the current authorization index
address space. The
with space switching (PT-ss) and SET
(SSAR-ss) and may be performed as part
of
authorization
instructions.
When performed as part of PT-ss, the
be established as the primary
performed as part of
established as the secondary
called secondary-ASN authorization.
The
means of an authority table in real
storage which is designated by the
authority-table-origin and authority
table-length fields
table entry.
table origin and the authority-table
length from the ASH-second-table entry,
together with an authorization index.
contents of control register 4 include
the authorization index. For
which will become the new contents of
control register 4;s used. The regis
ter has the following format:
AX
Authorization Index (AX): Bits
control register 4 are used as an index
to locate the authority bits in the
authority table.
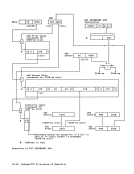
ASN-Second-Table Entry
The ASN-second-table entry which is
fetched as part of the
process contains information which is
used to designate the authority table.
An entry
following format:
00
ATl
0000
Authority-Table
8-29, with two zeros appended on the
right, are used to form
address that designates the beginning of
the authority table.
addressing, the authority-table origin