Storage Addressing
Information Formats
Integral Boundaries
Address Types
Absolute Address
Real Address
Virtual Address
Primary
Secondary Virtual Address
Instruction Address
Effective Address
Storage Key
Storage-Key 4K-Byte-Block Fac iIi ty
Storage Keys with Storage-Key 4K-Byte-Block
Facility Not Installed
Storage Keys with Storage-Key 4K-Byte-Block
Storage-Key-Exception
Storage-Key-Instruction Extensions
Protection
Segment Protection
low-Address Protection
Reference Recording
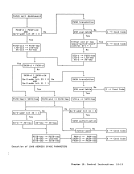
Address Spaces
ASH-Translation
ASN-Second-Table Entries
ASH-Translation Process
ASH-Second-Table lookup
Recognition of Exceptions during
ASH-Authorization
ASN-Second-Table Entry
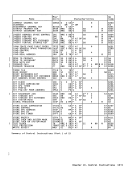
Authority-Table Entries ...........•................... 3-18
ASH-Authorization Process
Authority-Table lookup
Recognition of Exceptions during
Translation Modes
Translation Tables
Segment-Table
Page-Table
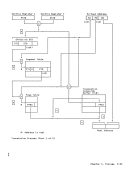
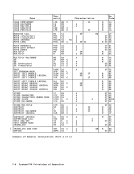
Summary of Dynamic-Address-Translation Formats
Translation Process
Effective Segment-Table Designation
Inspecti on of
Formation of the Real Address
Recognition of Exceptions during Translation
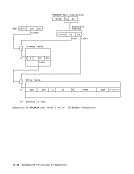
Translation-lookaside Buffer
Use of the Translation-lookaside Buffer
Modification of Translation Tables