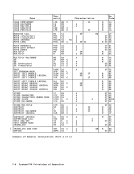
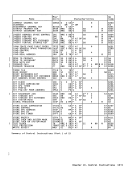
Each program then enters the address of
the elementwhich it has provided into the header, while simultaneously it
removes the address previously contained
in the header. Thus, associatedwith any particular program attempting to use
the SRR are two elements, called the
"entered element" and the "removed
element." The "entered element" of one
program becomes the "removed element"
for the immediately following program.
Each program then waits on the removedelement, uses the SRR, and then posts
the entered element.
When no contention occurs, that is, when
the second program does not attempt to
use the SRR until after the first
program is finished, then thePOST of
the first program occurs before the WAIT
of the second program. Inthis case,
the bypass-post and bypass-wait routines
described in the preceding section are
applicable. For simplicity, these two
routines are shown only by name rather
than as individual instructions.
In the example, the element need be only
a single word, that is, anECB. However, in actual practice, the element
could be made larger to include a point
er to the previous element, along with a
program identification. Such informa
tion would be useful in an error
situation to permit starting with the
header and chaining through the list of
elements to find the program currently
holding the SRR.
It should be noted that the element
provided by the program remains pointed
to by the header until the next program
attempts to lock. Thus, in general, the
entered element cannot be reused by the
program. However, the removed elementis available, so each program gives up
one element andgains a new one. It is expected that the element removed by a
particular program during one use of the
SRR would then be used by that program
as the entry element for the next
request to the SRR.
It should be noted that,since the
elements are exchanged from one program
to the next, the elements cannot be
allocated from storage that would be
freed and reused when the program ends.
Itis expected that a program would
obtain its first element and release its
last element by means of the routines
described in the section "Free-Pool
Manipulation"in this appendix.
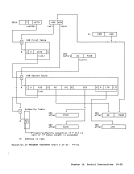
The following chart describes the action
taken forFIFO LOCK and FIFO UNLOCK. Function Action FIFO LOCK Store address A
into the header.
(the incoming WAIT; theECB is at
element is at the location addres-
location A) sed by the old con-
tents of the header.FIFO UNLOCK POST; the ECB is at
location A.
The following routines allow enabled
code to perform the actions described in
the previous chart.FIFO LOCK Routine:
Initial conditions:
GR3 contains the address of the header.
GR4 contains the address, A, of the
element currently owned by this
program. This element becomes the
entered element.FLOCK LR 2,4
SR
ST
LTRYAGN CS BC LR
1,1
1,0(2)1,0(3) 1,2,0(3) 7,TRYAGN HSWAIT
GR2 now contains
address of ele
ment to be
entered
GR1 =° Initialize the ECB GR1 = contents of
the header
Enter address Ainto header
while remember
ing old contents
of headerinto GR1; GR1 now
contains address
of removed
element
Removed element
becomes new cur
rently owned
element
Perform bypass-
wait rout i ne; if ECB already
posted, con-
t i nue; if not,wait; GR1 con
tains the ad
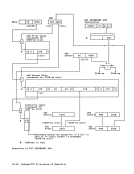
dress of theECB USE [Any instruction] FIFO UNLOCK Routine:
Initial conditions:
GR2 contains the address of the removed
element, obtained during theFLOCK routine.
GR5 contains40 00 00 00{16} Appendix A. Humber Representation and Instruction-Use Examples A-45
the element
removes the address previously contained
in the header. Thus, associated
the SRR are two elements, called the
"entered element" and the "removed
element." The "entered element" of one
program becomes the "removed element"
for the immediately following program.
Each program then waits on the removed
the entered element.
When no contention occurs, that is, when
the second program does not attempt to
use the SRR until after the first
program is finished, then the
the first program occurs before the WAIT
of the second program. In
the bypass-post and bypass-wait routines
described in the preceding section are
applicable. For simplicity, these two
routines are shown only by name rather
than as individual instructions.
In the example, the element need be only
a single word, that is, an
could be made larger to include a point
er to the previous element, along with a
program identification. Such informa
tion would be useful in an error
situation to permit starting with the
header and chaining through the list of
elements to find the program currently
holding the SRR.
It should be noted that the element
provided by the program remains pointed
to by the header until the next program
attempts to lock. Thus, in general, the
entered element cannot be reused by the
program. However, the removed element
one element and
particular program during one use of the
SRR would then be used by that program
as the entry element for the next
request to the SRR.
It should be noted that,
elements are exchanged from one program
to the next, the elements cannot be
allocated from storage that would be
freed and reused when the program ends.
It
obtain its first element and release its
last element by means of the routines
described in the section "Free-Pool
Manipulation"
The following chart describes the action
taken for
into the header.
(the incoming WAIT; the
element is at the location addres-
location A) sed by the old con-
tents of the header.
location A.
The following routines allow enabled
code to perform the actions described in
the previous chart.
Initial conditions:
GR3 contains the address of the header.
GR4 contains the address, A, of the
element currently owned by this
program. This element becomes the
entered element.
SR
ST
L
1,1
1,0(2)
GR2 now contains
address of ele
ment to be
entered
GR1 =
the header
Enter address A
while remember
ing old contents
of header
contains address
of removed
element
Removed element
becomes new cur
rently owned
element
Perform bypass-
wa
posted, con-
t i nue; if not,
tains the ad
dress of the
Initial conditions:
GR2 contains the address of the removed
element, obtained during the
GR5 contains