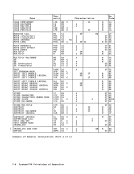
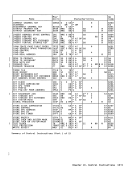
ly after fetching the first operand
byte. The entire rightmost second
operand byte is used in forming the
first result byte. For the remainder of
the field, information for two result
bytes is obtained from a single second
operand byte, and execution proceeds as
if the leftmost four bits of the byte
were to remain available for the next
result byte and need not be refetched.
Thus, the result is as if two result
bytes were to be stored immediately
after fetching a single operand byte.Condition Code: unchanged. Program Exceptions:
The code remains
Access (fetch, operand 2; store,
operand 1)Programming Notes
1. An example of the use of theUNPACK instruction is given in Appendix A.
2. A field that is to be unpacked can
be destroyed by improper·overlap ping. To save storage space for
unpacking by overlapping the oper
ands, the rightmost byte of the
first operand must be to the right
of the rightmost byte of the second
operand by the number of bytes in
the second operand minus 2. If
only one or two bytes are to be
unpacked, the rightmost bytes of
the two operands may coincide.
3. The storage-operand references ofUNPACK may be multiple-access
references. (See the section
"Storage-OperandConsistency" in Chapter 5, "Program Execution.~) Chapter 7. General Instructions 7-41
byte. The entire rightmost second
operand byte is used in forming the
first result byte. For the remainder of
the field, information for two result
bytes is obtained from a single second
operand byte, and execution proceeds as
if the leftmost four bits of the byte
were to remain available for the next
result byte and need not be refetched.
Thus, the result is as if two result
bytes were to be stored immediately
after fetching a single operand byte.
The code remains
Access (fetch, operand 2; store,
operand 1)
1. An example of the use of the
2. A field that is to be unpacked can
be destroyed by improper
unpacking by overlapping the oper
ands, the rightmost byte of the
first operand must be to the right
of the rightmost byte of the second
operand by the number of bytes in
the second operand minus 2. If
only one or two bytes are to be
unpacked, the rightmost bytes of
the two operands may coincide.
3. The storage-operand references of
references. (See the section
"Storage-Operand