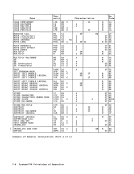
1 Selected bits mixed zeros and
ones
2
3 Selected bitsall ones Program Exceptions:
Access (fetch, operand 1)Programming Note
An example of the use of the TEST UNDER
MASK instruction is given in Appendix A.
TRANSLATE
TR [SS]'DC' L I B, I ~, B. I EJ o 8 16 20 32 36 47
The bytes of the first operand are used
as eight-bit arguments to reference alist designated by the second-operand
address. Each function byte selected
from the list replaces the corresponding
argument in the first operand.
The L field specifies the length of only
the first operand.
The bytes of the first operand are
selected one by one for translation,
proceeding left to right. Each argument
byte is added to the initial second
operand address. The addition is
performed following the rules for
address arithmetic, with the argument
byte treated as an eight-bit unsigned
binary integer and extended with zeros
on the left. The sum is used as the
address of the function byte, which then
replaces the original argument byte.
The operation proceeds until the first
operand field is exhausted. The list is
not altered unless an overlap occurs.
When the operands overlap, the result is
obtained as if each result byte were
stored immediately after fetching the
corresponding function byte.
Access exceptions are recognized only
for those bytes in the second operand
which are actually required.Condition Code: unchanged. Program Exceptions:
The code remains
Access (fetch, operand 2; fetch and
store, operand 1)Programming Notes
1. An example of the use of the TRANS
LATE instruction is given in Appen
dix A.
2. TRANSLATE may be used to convert
data from one code to another code.
3. The instruction may also be used to
rearrange data. This may be accom
plished by placing a pattern in the
destination area, by designating
the pattern as the first operand of
TRANSLATE, and by designating the
data that is to be rearranged as
the second operand. Each byte of
the pattern contains an eight-bit
number specifying the byte destined
for this position. Thus, when the
instruction is executed, the
pattern selects the bytes of the
second operand in the desired
order.
4. Because each eight-bit argument
byte is added to the initial
second-operand address to obtain
the address ofa function byte, the
list may contain 256 bytes. In
cases where it is known that not
all eight-bit argument values will
occur, it is possible to reduce the
size of the list.
5. Significant performance degradation
is possible when, withOAT on, the
second-operand address of TRANSLATE
designates a location that is less
than 256 bytes to the left of a
2K-byte boundary. This is because
the machine may perform a trial
execution of the instruction to
determine if the second operand
actually crosses the boundary.
6. The fetch and subsequent store
accesses to a particular byte in
the first-operand field do not
necessarily occur one immediately
after the other. Thus, this
instruction cannot be safely used
to update a location in storage if
the possibility exists that anotherCPU or a channel may also be updat ing the location. An example of
this effect is shown forOR (01) in
the section "Multiprogramming and
Multiprocessing Examples" in Appen
dix A.
7. The storage-operand references of
TRANSLATE may be multiple-access
references.(See the section
"Storage-Operand Consistency" inChapter 5, "Program Execution.") Chapter 7. General Instructions 7-39
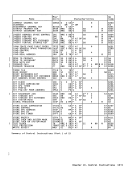
ones
2
3 Selected bits
Access (fetch, operand 1)
An example of the use of the TEST UNDER
MASK instruction is given in Appendix A.
TRANSLATE
TR [SS]
The bytes of the first operand are used
as eight-bit arguments to reference a
address. Each function byte selected
from the list replaces the corresponding
argument in the first operand.
The L field specifies the length of only
the first operand.
The bytes of the first operand are
selected one by one for translation,
proceeding left to right. Each argument
byte is added to the initial second
operand address. The addition is
performed following the rules for
address arithmetic, with the argument
byte treated as an eight-bit unsigned
binary integer and extended with zeros
on the left. The sum is used as the
address of the function byte, which then
replaces the original argument byte.
The operation proceeds until the first
operand field is exhausted. The list is
not altered unless an overlap occurs.
When the operands overlap, the result is
obtained as if each result byte were
stored immediately after fetching the
corresponding function byte.
Access exceptions are recognized only
for those bytes in the second operand
which are actually required.
The code remains
Access (fetch, operand 2; fetch and
store, operand 1)
1. An example of the use of the TRANS
LATE instruction is given in Appen
dix A.
2. TRANSLATE may be used to convert
data from one code to another code.
3. The instruction may also be used to
rearrange data. This may be accom
plished by placing a pattern in the
destination area, by designating
the pattern as the first operand of
TRANSLATE, and by designating the
data that is to be rearranged as
the second operand. Each byte of
the pattern contains an eight-bit
number specifying the byte destined
for this position. Thus, when the
instruction is executed, the
pattern selects the bytes of the
second operand in the desired
order.
4. Because each eight-bit argument
byte is added to the initial
second-operand address to obtain
the address of
list may contain 256 bytes. In
cases where it is known that not
all eight-bit argument values will
occur, it is possible to reduce the
size of the list.
5. Significant performance degradation
is possible when, with
second-operand address of TRANSLATE
designates a location that is less
than 256 bytes to the left of a
2K-byte boundary. This is because
the machine may perform a trial
execution of the instruction to
determine if the second operand
actually crosses the boundary.
6. The fetch and subsequent store
accesses to a particular byte in
the first-operand field do not
necessarily occur one immediately
after the other. Thus, this
instruction cannot be safely used
to update a location in storage if
the possibility exists that another
this effect is shown for
the section "Multiprogramming and
Multiprocessing Examples" in Appen
dix A.
7. The storage-operand references of
TRANSLATE may be multiple-access
references.
"Storage-Operand Consistency" in