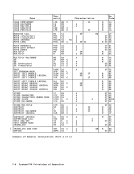
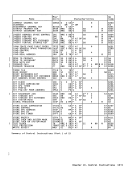
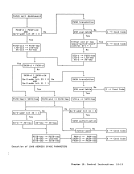
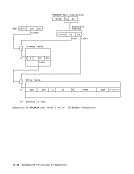
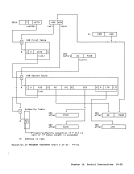
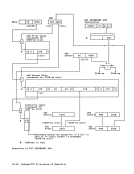
When the access to storage is for the
purpose of channel-program execution,
the subchannel key associated with theI/O operation is the access key. The
subchannel key is specified for anI/O operation in bit positions 0-3 of the
channel-address word(CAW); the subchan
nel key is later placed in bit positions0-3 of the channel-status word (CSW) stored as a result of the I/O operation.
When aCPU access is prohibited because
of key-controlled protection, the unit
of operationis suppressed or the
instruction is terminated, and a program
interruption for a protection exception
takes place. When a channel-program
accessis prohibited, protection check
is indicated in theCSW stored as a
result of the operation.
When a store access is prohibited
because of key-controlled protection,
the contents ofthe protected location
remain unchanged. When a fetch access
is prohibited, the protected information
is not loaded into a register, moved to
another storage location, or provided to
anI/O device. For a prohibited
instruction fetch, the instruction is
suppressed, and an arbitrary
instruction-length code is indicated.
Key-controlled protection is independent
of whether theCPU is in the problem or
the supervisorstate and, except as
described below, does not depend on the,type of CPU instruction or channel
command word being executed.I \ , Except where otherwise specified, all
accesses to storage locations that are
explicitly designated bythe program and
that are used by theCPU to store or
fetch information are subject to key
controlled protection.
Accesses to the second operand of TESTBLOCK are not subject to key-controlled
protection.
All storage accesses by a channel to
fetch aCCW or IDAW or to access a data
area designated duringthe execution of
aCCW, are subject to key-controlled
protection. However, if aCCW, an IDAW,
or output data is prefetched,a protection check is not indicated until
theCCW or IDAW is due to take control
or until the data is due to be written.
Key-controlled protection is not applied
to accesses that are implicitly made for
any of such sequences as:• An interruption • Updating the interval timer • CPU logout • Fetching of table entries
dynamic-address translation,
forPC- • • • • • • • number translation, ASN transla
tion, orASN authorization
DAS tracing
A store-status function
Fetching theCAW during the
execution of anI/O instruction
Storing of theCSW by an I/O instruction or interruption
Storing channel identification
during the execution ofSTORE CHAN NEL ID
A limited channel logout
A full channel logout• Initial program loading
Similarly, protection does not apply to
accesses initiated via the operator
facilities for altering or displaying
information. However, when the program
explicitly designates these locations,
they are subject to protection.
SEGMENTPROTECTION The segment-protection facility controls
access to virtual storage by using the
segment-protection bit in each segment
table entry. It provides protection
against improper storing.
The segment-protection bit, bit 29 of
the segment-table entry, controls whether storing is allowed into the corre
sponding segment.When the bit is zero,
both fetching and storing are permitted;
when the bitis one, only fetching is
permitted. When an attempt is made to
store into a protected segment, a
program interruption for protection
takes place. The contents of the
protected location remain unchanged.
Segment protection applies to all
store-type references thatuse a virtual
address.LOW-ADDRESS PROTECTION The low-address-protection facility pro
vides protection against the destruction
of main-storage information used by theCPU during interruption processing.
This is accomplished by prohibiting
instructions from storing with effective
addresses in the range0 through 511. The range criterion is applied before
address transformation,if any, of the
address by dynamic address translation
or prefixing.Chapter 3. Storage 3-9
purpose of channel-program execution,
the subchannel key associated with the
subchannel key is specified for an
channel-address word
nel key is later placed in bit positions
When a
of key-controlled protection, the unit
of operation
instruction is terminated, and a program
interruption for a protection exception
takes place. When a channel-program
access
is indicated in the
result of the operation.
When a store access is prohibited
because of key-controlled protection,
the contents of
remain unchanged. When a fetch access
is prohibited, the protected information
is not loaded into a register, moved to
another storage location, or provided to
an
instruction fetch, the instruction is
suppressed, and an arbitrary
instruction-length code is indicated.
Key-controlled protection is independent
of whether the
the supervisor
described below, does not depend on the
command word being executed.
accesses to storage locations that are
explicitly designated by
that are used by the
fetch information are subject to key
controlled protection.
Accesses to the second operand of TEST
protection.
All storage accesses by a channel to
fetch a
area designated during
a
protection. However, if a
or output data is prefetched,
the
or until the data is due to be written.
Key-controlled protection is not applied
to accesses that are implicitly made for
any of such sequences as:
dynamic-address translation,
for
tion, or
DAS tracing
A store-status function
Fetching the
execution of an
Storing of the
Storing channel identification
during the execution of
A limited channel logout
A full channel logout
Similarly, protection does not apply to
accesses initiated via the operator
facilities for altering or displaying
information. However, when the program
explicitly designates these locations,
they are subject to protection.
SEGMENT
access to virtual storage by using the
segment-protection bit in each segment
table entry. It provides protection
against improper storing.
The segment-protection bit, bit 29 of
the segment-table entry, controls wheth
sponding segment.
both fetching and storing are permitted;
when the bit
permitted. When an attempt is made to
store into a protected segment, a
program interruption for protection
takes place. The contents of the
protected location remain unchanged.
Segment protection applies to all
store-type references that
address.
vides protection against the destruction
of main-storage information used by the
This is accomplished by prohibiting
instructions from storing with effective
addresses in the range
address transformation,
address by dynamic address translation
or prefixing.