Special Conditions Since the secondary space is accessed,
the operation is performed only whenthe secondary-space control, bit 5 of
control register0, is one and OAT is
on.When either the secondary-space
control is zero orOAT is off, a
special-operation exception is recog
nized. The special-operation exception
is recognized in boththe problem and
supervisor states.
In the problem state,the operation is
performed only if the secondary-space
accesskey is valid, that is, if the
corresponding PSW-key-mask bit in
control register 3 is one.Otherwise, a
privileged-operation exception is recog
nized. In the supervisor state, any
value for the secondary-space access key
is valid.
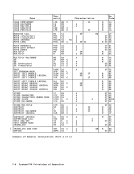
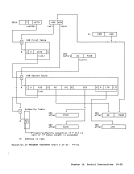
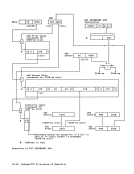
The priority of the recognition of
exceptions and condition codes is shown
1n the figure "Priority of Execution:MOVE TO PRIMARY and MOVE TO SECONDARY." Resulting Condition Code: o True length less than or equal
to 256
1
2
3 True length greater than 256
Program Exceptions:
Access (fetch, primary virtual ad
dress, operand2, MVCS; fetch,
secondary virtual address, op
erand 2,MVCPi store, secondary
virtual address, operand 1,MVCSj store, primary virtual
address, operand1, MVCP) Operation (if the dual-address-
space facility is not
installed)
Privileged operation (selected
PSW-key-mask bit iszero in the problem state)
Special operation
1.-6. Exceptions with the same pri
ority asthe priority of pro
gram-interruption conditions
for the general case.
7.A Access exceptions for second
and third instruction half
words.
7.B.1Operation exception if the dual-address-space facility is
not installed.
7.B.2 Special-operation exception due
tothe secondary-space control,
bit 5 of control register0, being zero or to OAT being off.
8. Privileged-operation exception
due to selected PSW-key-mask
bit being zero inthe problem
state.
9.10. Completion due to length zero.
Access exceptions for operands.
Priority of Execution:MOVE TO PRIMARY and MOVE TO SECONDARY Programming Notes
1.MOVE TO PRIMARY and MOVE TO SECOND ARY can be used in a loop to move a
variable number of bytes of any
length.See the programming note
underMOVE WITH KEY. 2. MOVE TO PRIMARY and MOVE TO SECOND ARY should be used only when move
ment is between different address
spaces. The performance of these
instructions on most models may be
significantly slower thanMOVE WITH KEY, MOVE (MVC), or MOVE LONG. In
addition, the definition of over
lapping operands forMOVE TO PRIMARY and MOVE TO SECONDARY is
not compatible with the more
precise definitions forMOVE (MVC), MOVE WITH KEY, or MOVE LONG. Chapter 10. Control Instructions 10-23
the operation is performed only when
control register
on.
control is zero or
special-operation exception is recog
nized. The special-operation exception
is recognized in both
supervisor states.
In the problem state,
performed only if the secondary-space
access
corresponding PSW-key-mask bit in
control register 3 is one.
privileged-operation exception is recog
nized. In the supervisor state, any
value for the secondary-space access key
is valid.
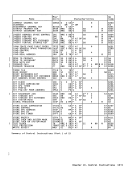
The priority of the recognition of
exceptions and condition codes is shown
1n the figure "Priority of Execution:
to 256
1
2
3 True length greater than 256
Program Exceptions:
Access (fetch, primary virtual ad
dress, operand
secondary virtual address, op
erand 2,
virtual address, operand 1,
address, operand
space facility is not
installed)
Privileged operation (selected
PSW-key-mask bit is
Special operation
1.-6. Exceptions with the same pri
ority as
gram-interruption conditions
for the general case.
7.A Access exceptions for second
and third instruction half
words.
7.B.1
not installed.
7.B.2 Special-operation exception due
to
bit 5 of control register
8. Privileged-operation exception
due to selected PSW-key-mask
bit being zero in
state.
9.
Access exceptions for operands.
Priority of Execution:
1.
variable number of bytes of any
length.
under
ment is between different address
spaces. The performance of these
instructions on most models may be
significantly slower than
addition, the definition of over
lapping operands for
not compatible with the more
precise definitions for