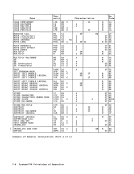
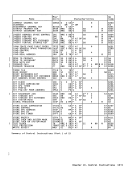
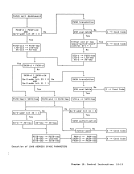
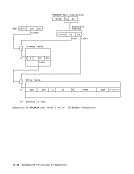
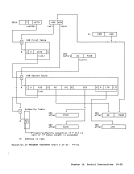
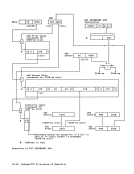
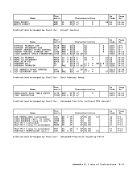
Correction of Machine Malfunctions
Error
Effects of
Handling of Machine
Checkpoint-Synchronization Operations
Checkpoint-Synchronization Action
Unit Deletion
Handling of Machine
Validation
Invalid
Programmed Validation of Storage
Invalid
Invalid
System
Machine-Check Interruption
Exigent
Repressible
Interruption Action
Point of Interruption
Machine-Check-Interruption
Subclass
System Damage
Instruction-Processing Damage
System Recovery
Interval-Timer Damage
Timing-Facility Damage
External Damage
Vector-Facility Failure
Degradation
Warning
Service-Processor Damage
Subclass Modifiers
Vector-Facility Source
Backed Up
Delayed
Delayed Access Exception
Synchronous Machine-Check-Interruption Conditions
Processing Backup
Processing Damage
Storage Errors
Storage Error Uncorrected
Storage Error
Storage Degradation
Indirect Storage Error
PSW-EMWP Validity
PSW Mask and Key Validity
PSW-Instruction-Address Validity
Failing-Storage-Address Validity
External-Damage-Code Validity
Floating-Point-Register Validity
General-Register Validity
Control-Register Validity
Logout Validity
Storage Logical Validity
Machine-Check Extended-Logout Length
Register-Save Areas