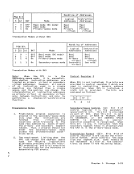
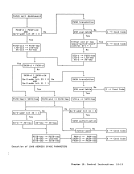
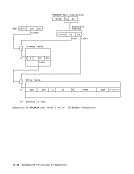
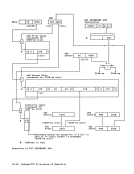
ASH-Second-Table Entry
I ATO STD LTL
(x4)
Authority Table
R
p S
For primary
zero or table length exceeded.
For secondary
Secondary-authority exception
For secondary
Set condition code 2
table length exceeded.
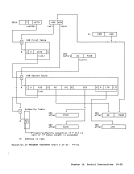
R: Address
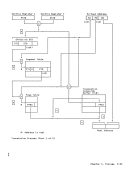
Authority-Table Lookup
The authorization
with the authority-table orlg1n
contained in the ASH-second-table entry,
authority table.
The authorization index
bit positions
4.
is contained in
control register
Bit positions 8-31 of
contain the 24-bit real address of the
authority table (ATO), and bit positions
48-59 contain the length of the authori
ty table (ATL).
authority-table orlgln and adding the 14
leftmost bits of the authorization index
with
carry, if any, into bit position 7
this 24-bit real address is extended on
the left
table can wrap from
As part of the authority-table-entry
lookup process, bits
authority-table length. If the compared
portion
table length,
exception or secondary-authority excep
tion
length is exceeded, condition code 2 is
set.
Chapter 3. Storage 3-19